In this video, we're going to explore the new features of application visibility in ISE 2.2 and go through regular posturing configuration in ISE. The Cisco AnyConnect ISE Posture agent runs on the endpoint. Upon initial connection the client authenticates to ISE and is matched against a Posture Unknown Authorization Policy, the AnyConnect module connects to ISE and receives the posture requirements. ISE provisions AnyConnect Posture Module and Compliance Module. After the agent is installed on the client machine, it automatically searches for ISE by sending probes. When ISE is detected successfully, posture requirements are checked on the endpoint. AnyConnect Specific Features. AnyConnect is more than just a VPN client. It is a fully-fledged end-point mobility client solution. However, unlike the AnyConnect implementation on the ASA or FirePOWER with support for multiple features like Host scan, Web launch, etc, the MX security appliance supports SSL Core VPN and other AnyConnect modules that do not require additional configuration on.
Came across this task to set up a posture assessment for workstation domain membership check when connecting with Anyconnect (AC) VPN to Cisco ASA and enforce access based on compliance. ISE was already deployed for simple VPN authentication so, first of all, I had to make a decision on what to use: ASA host scan (requires ASA APEX license) or ISE posture assessment. Great feature comparison here but if it comes down to price then it is about $10 versus $7 per user for ASA vs ISE. And since ISE offers more flexibility it was picked for the final solution.
There are a few Cisco 1, 2 and non Cisco guides there so here I’ll just fill in missing pieces.
- Get APEX license to support posture for ISE in addition to Base License which you should have already.
- Upload and enable proper AC package on ASA. The package you need is anyconnect-….webdeploy-k9.pkg. All necessary files will be included in it. At the time of writing, my file version was anyconnect–win-4.6.04056-webdeploy–k9.pkg. Once file is uploaded use this command to enable it.

webvpn
anyconnect-win-4.6.04056-webdeploy-k9.pkg 1
- Enable ISE posture module to be installed on the endpoint.
group-policy DfltGrpPolicy attributes
webvpn
anyconnect modules value iseposture
- Create ACL on ASA to allow DNS requests and traffic to ISE nodes. Redirect all other web traffic for posture to take place.
access-list redirect extended deny udp any any eq domain
access-list redirect extended deny ip any host <ISE IP>
access-list redirect extended permit tcp any any eq www
- Add dynamic authorization under ISE aaa-server group
aaa-server ISE protocol radius
authorize-only
interim-accounting-update periodic 1
dynamic-authorization
- Make sure accounting is enabled under default tunnel-group
tunnel-group DefaultWEBVPNGroup general-attributes
authentication-server-group ISE
accounting-server-group ISE
This will conclude ASA configuration.
Some good debugging commands to troubleshoot posture-related issues on ASA.
- debug aaa url-redirect
- debug aaa authorization
- debug radius dynamic-authorization
- debug radius decode
- debug radius user <USERNAME>
- show vpn-sessiondb detail anyconnect filter name <USERNAME>
Now move on to ISE.
First get you latest posture updates. Administration> System> Settings> Posture> Updates.
Anyconnect Posture Agent Login
Make sure your posture portal is setup with publicly signed certificate otherwise users will get trust errors. With some providers, you can not generate a wildcard certificate so you will have to include all Policy Service Nodes (PSN) FQDN as a separate SAN field in CSR or generate individual certificate per node. When done attach certificate to proper Portal group.
Configure the following elements for Client Provisioning under Work Centers > Posture> Client Provisioning > Resources
- Posture Agent Profile. Populate Discovery host with PSN FQDNs and Call Home list with PSN FQDNs and IP addresses.
- Next upload AC package to ISE. This is the anyconnect-…predeploy-k9.zip file that you can find on Cisco AC download page. Select “Agent resources from local disk“. Make sure and give a meaningful name so it will be easier to identify.
AC version on ISE has to match the one on ASA otherwise you will get an error message.
- Download the latest compliance modules from Cisco for Windows/OSX and Supplicant Provisioning Wizard.
- Finally, create AnyConnect configuration for use in client provisioning policy.
AC configuration settings are below.
- Create Client Provisioning Policy under Policy> Client Provisioning
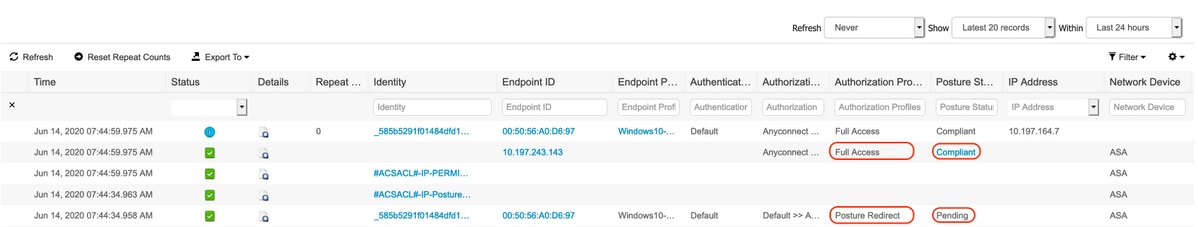
Next, build a Posture Policy. I’m not going to cover different posture checks at this time. Remember on the policy there is an option to put it in audit mode so you can test it out before enforcing.
Since ISE reporting is not the greatest for customization and flexibility I’m using Splunk searches to get quick reports. How to get ISE logs into Splunk I covered in this post.
Today applications are evolving and moving to the public cloud. Amazon Web Services (AWS) offers different types of services to host these applications in the cloud. Customers are opting for hybrid cloud services because it provides the optimum architecture for application hosting and performance. This change in cloud architecture introduces a big challenge of providing a secure connection to the remote workers.
Cisco provides a comprehensive solution by offering Cisco Adaptive Security Appliance (ASAv) and Cisco Next-Generation Firewall in the AWS marketplace. These virtual appliances can integrate with the Cisco security portfolio and provides unmatched remote access VPN architecture for AWS.
Figure 1: Components of the Cisco Secure Remote Worker
Cisco Anyconnect Ise Posture Module
- Cisco AnyConnect Secure Mobility Client:Cisco AnyConnect Secure Mobility Client empowers remote workers with frictionless, highly secure access to the enterprise network from any device, at any time, in any location while protecting the organization. It provides a consistent user experience across devices, both on and off-premises, without creating a headache for your IT teams. Simplify management with a single agent.
- Cisco Duo:Cisco Duo is a user-friendly, scalable way to keep business ahead of ever-changing security threats by implementing the Zero Trust security model. Multi-factor authentication from Duo protects the network by using a second source of validation, like a phone or token, to verify user identity before granting access. Cisco Duo is engineered to provide a simple, streamlined login experience for every remote user. As a cloud-based solution, it integrates easily with your existing technology and provides administrative, visibility, and monitoring.
- Cisco Umbrella Roaming Security Module: Cisco Umbrella Roaming Security module for Cisco AnyConnect provides always-on security on any network, anywhere, any time — both on and off your corporate VPN. The Roaming Security module enforces security at the DNS layer to block malware, phishing, and command and control callbacks over any port. Umbrella provides real-time visibility into all internet activity per hostname both on and off your network or VPN.
- Cisco Advanced Malware Protection (AMP) Enabler:Cisco AnyConnect AMP Enabler module is used as a medium for deploying Advanced Malware Protection (AMP) for Endpoints. It pushes the AMP for Endpoints software to a subset of endpoints from a server hosted locally within the enterprise and installs AMP services to its existing user base. This approach provides AnyConnect user base administrators with an additional security agent that detects potential malware threats happening in the network, removes those threats, and protects the enterprise from compromise. It saves bandwidth and time taken to download, requires no changes on the portal side, and can be done without authentication credentials being sent to the endpoint. AnyConnect AMP Enabler protects the user both on and off the network or VPN.
- Cisco Identity Services Engines (ISE):Cisco AnyConnect Secure Mobility Client offers a VPN posture module and an ISE posture module. Both provide the Cisco AnyConnect Secure Mobility Client with the ability to assess an endpoint’s compliance for things like antivirus, antispyware, and firewall software installed on the host. The administrator can then restrict network access until the endpoint is in compliance.
- Cisco Adaptive Security Appliance (Virtual Appliance):The Cisco Adaptive Security Appliance (ASA) is a security appliance that protects corporate networks and data centers. It provides users with highly secure access to data and network resources – anytime, anywhere. The remote users can use Cisco AnyConnect Secure Mobility Client on the endpoints to securely connect to the resources hosted in the Data Center or the Cloud.
- Cisco Next-Generation Firewall / Firepower Threat Defense (Virtual Appliance):The Cisco Firepower NGFW helps you prevent breaches, get visibility to stop threats fast, and automate operations to save time. A next-generation firewall (NGFW) is a network security device that provides capabilities beyond a traditional, stateful firewall by adding capabilities like application visibility and control, Next-Generation IPS, URL filtering, and Advanced Malware Protection (AMP).
Due to layer-2 abstraction in the cloud, it not possible to provide native firewall high availability, firewall clustering, and VPN clustering. AWS offers native services like AWS route53, AWS route tables that enable DNS based load balancing.
Traffic Flow:
- The remote access VPN user initiates a VPN connection using a hostname (example: answamivpn.com), and the DNS server returns an IP address. AWS route53 monitors all the firewalls using AWS route53 health checks
- Remote user makes the connection to the firewall
- Access the resources hosted in AWS
Recommendation for the architecture shown in figure 2:
- Each availability zone (AZ) should have multiple firewalls (ASAv or NGFWv)
- Each firewall should have a dedicated VPN pool (i.e. separate VPN pool for each firewall)
- VPN pool should be outside of VPC CIDR range, avoid overlapping networks
- Control traffic using AWS route table
- Enable weighted average load balancing on AWS route53
- AWS route53 should track firewalls public IP/elastic IP using port 443
- Cisco Duo: Multi-factor authentication
- Cisco Umbrella Roaming Security Module: DNS layer security and IP enforcement
- Cisco AMP enabler: File and Malware analysis
- Cisco ISE: Authentication and Posture
- SWC: Visibility

The architecture shown in figure 2, is a scalable and resilient design for a single VPC deployment. This architecture is based on the principle of a distributed architecture. In the case of a multiple VPN architecture, we recommend deploying bigger firewall instances (example: C5.2xl 0r C5.4xl) in a centralized VPC.

In the case of a multi-vpc architecture, we recommend deploying multiple instances of bigger firewalls in a centralized VPC (known as security-hub VPC) and the connect security-hub VPC to spoke VPCs using AWS Transit Gateway.
The AWS transit gateway can have the following types of attachments:
- VPC attachment (used for VPC and AWS Direct Connect (DX) connection)
- VPN attachment (used for IPsec connectivity to DC)
- Peering connection (used for peering two AWS transit gateway – not shown in this architecture)
Traffic Flow:
- The remote access VPN user initiates a VPN connection using a hostname (example: answamivpn.com), and the DNS server returns an IP address. AWS route53 monitors all the firewalls using AWS route53 health checks.
- Remote user makes the connection to the firewall.
- Access the resources hosted in AWS.
Recommendation for the architecture shown in figure 3:
- Each availability zone (AZ) should have multiple firewalls (ASAv or NGFWv)
- Each firewall should have a dedicated VPN pool (i.e. separate VPN pool for each firewall)
- VPN pool should be outside of VPC CIDR range, avoid overlapping networks
- Control traffic using AWS route table
- Enable weighted average load balancing on AWS route53
- Use AWS Transit Gateway for interconnecting VPC
- For a hybrid cloud architecture, terminate VPN on the firewalls at the edge in the secure hub vpc or use VPN attachment on the AWS transit gateway.
- AWS route53 should track firewalls public IP/elastic IP using port 443
- Cisco Duo: Multi-factor authentication
- Cisco Umbrella Roaming Security Module: DNS layer security and IP enforcement
- Cisco AMP enabler: File and Malware analysis
- Cisco ISE: Authentication and Posture
- SWC: Visibility
Detailed information on the architecture described in figure3 is available this video: https://www.youtube.com/watch?v=ReI6I0eWyKc
In addition to the above information, we recommend checking out our Cisco Secure Remote Worker design guide that addresses a specific use case of remote access VPN connection covered in the SAFE Internet Edge Architecture Guide. The design for remote access VPN connections includes the Cisco AnyConnect Secure Mobility Client, Cisco Duo, Cisco Umbrella, and Cisco Advanced Malware Protection (AMP) for Endpoints.
Design Guide: https://www.cisco.com/c/dam/en/us/solutions/collateral/enterprise/design-zone-mobility/secure-remoteDe-worker-design-guide.pdf
Thanks,
Anubhav Swami (CCIEx2: 21208)
Security Solutions Architect
Cisco Systems Inc.
Cisco Blog: https://blogs.cisco.com/author/anubhavswami
YouTube Channel: https://www.youtube.com/anubhavswami
Reference links:
Cisco SAFE design guide for AWS: https://www.cisco.com/c/dam/en/us/solutions/collateral/enterprise/design-zone-security/secure-aws-design.pdf
Cisco SAFE Cloud Architecture Guide: https://www.cisco.com/c/dam/en/us/solutions/collateral/design-zone/cisco-validated-profiles/safe-secure-cloud-architecture-guide.pdf
Cisco SAFE secure remote worker: https://www.cisco.com/c/dam/en/us/solutions/collateral/enterprise/design-zone-mobility/secure-remote-worker-design-guide.pdf
Cisco Stealthwatch Cloud: https://www.cisco.com/c/en/us/products/security/stealthwatch-cloud/index.html
Cisco AMP for Endpoints: https://www.cisco.com/c/en/us/products/security/amp-for-endpoints/index.html
Cisco Duo: https://duo.com/
Cisco Umbrella: https://umbrella.cisco.com/
Cisco ASA: https://www.cisco.com/c/en/us/products/security/asa-firepower-services/index.html
Cisco Next-Generation Firewall: https://www.cisco.com/c/en/us/products/security/firewalls/index.html
Amazon Web Service: https://aws.amazon.com/
Amazon Load Balancer: https://aws.amazon.com/elasticloadbalancing/
Amazon Route53: https://aws.amazon.com/route53/
Amazon Route Table: https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Route_Tables.html
Amazon Transit Gateway: https://aws.amazon.com/transit-gateway/
Cisco Live Sessions:
NGFWv and ASAv in AWS and Azure (BRKSEC-2064): https://www.ciscolive.com/global/on-demand-library.html?search=Anubhav%20Swami#/session/1542224327848001r3qI
Deploy ASAv and NGFWv in AWS and Azure (LTRSEC-3052): https://www.ciscolive.com/global/on-demand-library.html?search=Anubhav%20Swami#/session/1564527389250001ckvR
ARM yourself using NGFWv and ASAv in Azure (BRKSEC-3093): https://www.ciscolive.com/global/on-demand-library.html?search=Anubhav%20Swami#/session/1560880389440001ntSs
See Full List On Cisco.com
YouTube Videos:
YouTube Channel: https://www.youtube.com/anubhavswami
