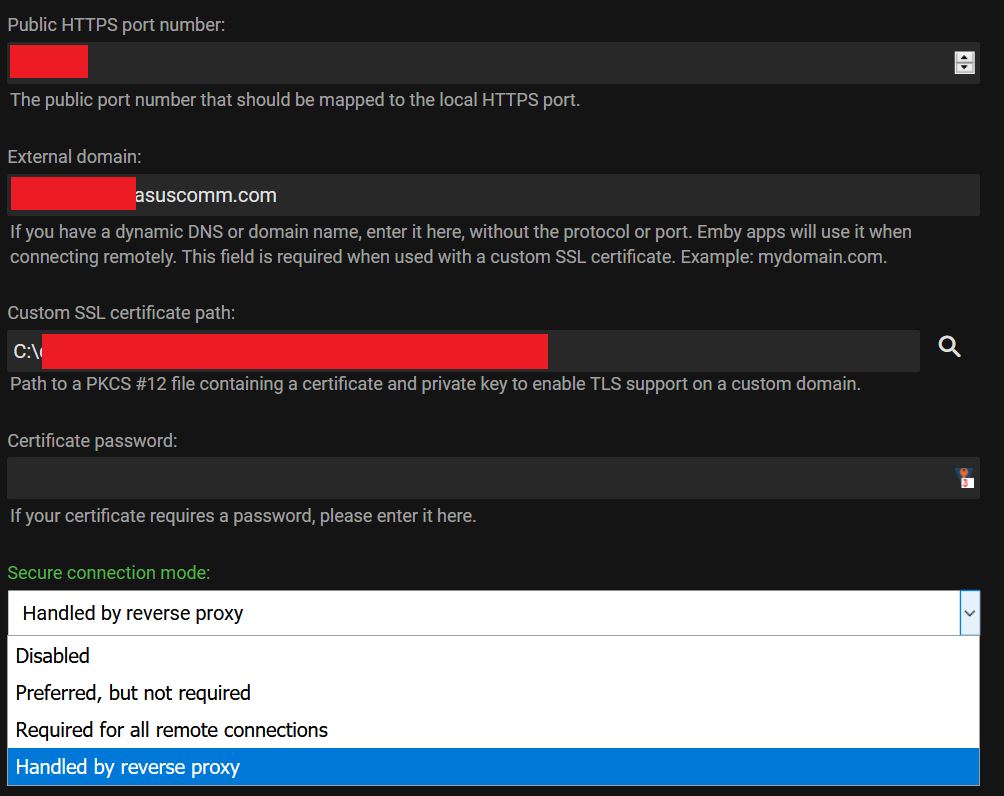
- Mozilla_pkix_error_ca_cert_used_as_end_entity
- Fehlercode Mozilla_pkix_error_ca_cert_used_as_end_entity
Today we’re excited to announce a new certificate verification library for Mozilla Products – mozilla::pkix! While most users will not notice a difference, the new library is more robust and maintainable. Organ trailclout games. The new code is more robust because certificate path building attempts all potential trust chains for a certificate before giving up (acknowledging the fact that the certificate space is a cyclic directed graph and not a forest). The new implementation is also more maintainable, with only 4,167 lines of C++ code compared to the previous 81,865 lines of code which had been auto-translated from Java to C. The new library benefits from C++ functionality such as memory cleanup tools (e.g., RAII).
To provide some more background, Gecko has historically used the certificate verification processing in NSS to ensure that the certificates presented during a TLS/SSL handshake is valid. NSS currently has two code paths for doing certificate verification: “classic” used by Gecko for Domain Validated (DV) certificate verification, and libPKIX used by Gecko for Extended Validation (EV) certificate verification. The NSS team has wanted to replace the “classic” verification with libPKIX for some time because libPKIX handles cross-signed certificates better and properly handles certificate policies required for Enhanced Validation (EV) certificates. However, libPKIX has proven to be very difficult to work with.
Mozilla_pkix_error_ca_cert_used_as_end_entity
Bug 1040446 - mozilla::pkix: add error code for CA cert used as end-entity cert. R=briansmith, a=lmandel. MOZILLAPKIXERRORCACERTUSEDASENDENTITY = The server uses a certificate with a basic constraints extension identifying it as a certificate authority. The root signing certificate ('GTE CyberTrust Global Root') was removed in Firefox 36. No version of Firefox from 36 on will trust certificates that depend on that root. You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. To refresh your session.
We also took the opportunity to enforce some requirements in Mozilla’s CA Certificate Policy and in the CA/Browser Forum’s Baseline Requirements (BRs). The changes are listed here. While we have performed extensive compatibility testing, it is possible that your website certificate will no longer validate with Firefox 31. This should not be a problem if you use a certificate issued by one of the CAs in Mozilla’s CA Program, because they should already be issuing certificates according to Mozilla’s CA Certificate Policy and the BRs. If you notice an issue due to any of these changes, please let us know.
We are looking for feedback with respect to compatibility and security. For compatibility, we ask all site operators and security testers to install Firefox 31 and use it to browse to your favorite sites. In addition, we ask for willing C++ programmers out there to review our code. This new mozilla::pkix library is located at security/pkix and security/certverifier. A more detailed description is here. If you find an issue, please help us make it better by filing a Bugzilla bug report.
We look forward to your feedback on this new certificate verification library.

Mozilla Security Engineering Team My summer of make.
Fehlercode Mozilla_pkix_error_ca_cert_used_as_end_entity
This site uses an invalid security certificate.
The certificate is not trusted because it is self signed.
(Error code: sec_error_untrusted_issuer)
--- Go to Tools --> Options in the menu bar of firefox.
--- Now click on the Advanced tab
--- Now click on the Certificates tab and then on the View Certificates button.
--- Now click on the Add Exception. You will see the following screen.
Here add the site you want to get the certificate to. Then click on get certificate. Firefox will check for the certificate and show it.
--- Now select Permanently store this exception and then press Confirm Security Exception.
That's it you will no longer get the self signed security certificate error for that site. You can also add other such sites following the above steps.