This chapter explains how to install Cygwin and start the SSH daemon on Microsoft Windows hosts. This chapter is applicable only when you want to install a Management Agent on a Microsoft Windows host, using the Add Host Targets Wizard or EM CLI. In particular, this chapter covers the following:
Important:
If you do not want to install Cygwin to deploy Management Agents on Microsoft Windows hosts using the Add Host Targets Wizard or EM CLI, you can choose to deploy Management Agents on these hosts using the PsExec process utility. For information on how to deploy Management Agents on Microsoft Windows hosts using PsExec, see Appendix F.Sshd is the OpenSSH server process. It listens to incoming connections using the SSH protocol and acts as the server for the protocol. It handles user authentication, encryption, terminal connections, file transfers, and tunneling. After making changes to the /etc/ssh/sshdconfig file, save the file, and restart the sshd server application to effect the changes using the following command at a terminal prompt: sudo systemctl restart sshd.service Warning. Many other configuration directives for sshd are available to change the server application’s behavior to fit your needs. If you still want to restart it, Ubuntu calls the service ssh, not sshd. Service ssh restart But if its not Ubuntu Desktop, using CLI: sudo systemctl restart ssh sudo service ssh restart The service is also controlled by upstart, and not sysvinit. So you'll find it at /etc/init/ssh.conf instead of /etc/init.d/ssh. Redirecting to /bin/systemctl restart sshd.service In the above CentOS 7 server you can see that “service sshd restart” command gets redirected to new command “systemctl restart sshd.service”. SSH Service is restarted but it shows from now on you should use “systemctl” command to restart instead of using ‘service’ command.
5.1About the Cygwin Requirement for Installing Management Agents
The Add Host Targets Wizard is an application built into the Enterprise Manager Cloud Control console. It offers GUI-rich, interactive screens that enable you to install Oracle Management Agents (Management Agents) on unmanaged hosts and convert them to managed hosts, so that they can be monitored and managed in Enterprise Manager Cloud Control.
When you use the Add Host Targets Wizard or EM CLI to install a Management Agent on a host running on Microsoft Windows, as a prerequisite, you must install Cygwin and start the SSH Daemon on the host. To do so, follow the steps listed in Section 5.3.
Cygwin is essentially a utility that offers a Linux-like environment on a Microsoft Windows host. Technically, it is a DLL (cygwin1.dll) that acts as a Linux API layer providing substantial Linux API functionality. Once you install Cygwin, you can configure the SSH Daemon on the host. The Add Host Targets Wizard is certified and supported with Cygwin 1.7.
The SSH Daemon enables the Add Host Targets Wizard to establish SSH connectivity between the OMS host and the host on which you want to install a Management Agent. Using this connectivity, the wizard transfers the Management Agent software binaries to the destination host over SSH protocol, installs the Management Agent, and configures it.
5.2 Before You Begin Installing Cygwin
Before starting with the SSHD setup, ensure you are not using OpenSSH and MKSNT when using the Add Host Targets Wizard. To do so, perform the following checks:
Ensure
OpenSSHbinandmksntare not in yourPATHenvironment variable. If they are, remove them by doing the following:Contact infomac drama. Right-click on My Computer and go to Properties.
In the System Properties window, click Advanced.
In this tab, click Environment Variables.
Here, search for the
PATHsystem variable, select it, and if theOpenSSHbinandmksntare present inPATH,click Edit.In the Edit System Variable dialog box, delete these two values from
PATH,then click OK.
Stop the SSH Daemon if it is running from
OpenSSH,MKSor any other vendor. If the SSH Daemon is running, stop it by doing the following:Right-click on My Computer, and select Manage.
In the Computer Management window, in the left pane, expand Services and Applications, and select Services.
In the right pane, click the SSH Daemon/MKS Secure Shell service, then click the Stop button.
Note:
The navigational steps described in this section may vary for different Microsoft Windows operating systems.5.3 Installing Cygwin
To install Cygwin on a Microsoft Windows host, follow these steps:
Access the following URL, then click Install Cygwin:
Download the 32-bit version (if you are running a 32-bit version of Microsoft Windows) or the 64-bit version (if you are running a 64-bit version of Microsoft Windows) of the Cygwin setup executable.
Run the setup executable, then click Next to proceed.
On the Choose Installation Type screen, select Install from Internet, then click Next.
On the Choose Installation Directory screen, enter C:cygwin as the Root Directory, then click Next.
Note:
If you choose to install Cygwin in a different directory, then ensure that you update theSSH_PATH, SCP_PATH, MKDIR_PATH, SH_PATH, CHMOD_PATH, andTRUEproperties present in the$<OMS_HOME>ouiprovresourcesssPaths_msplats.propertiesfile to their proper Cygwin binary values, after installing the Enterprise Manager system.For example, if you choose to install Cygwin in the
D:softwarecygwindirectory, then update the specified properties in the following manner:On the Select Local Package Directory screen, select a directory on your local machine where you want to store the downloaded installation files, then click Next.
On the Select Connection Type screen, select appropriate settings to connect to the internet, then click Next.
On the Choose Download Site(s) screen, select any site from the available list, then click Next.
On the select packages screen, ensure that you select the following packages, then click Next:
From the Archive category, select
unzipandzipas follows:From the Net category, select
opensshandopensslas follows:After selecting the packages and clicking Next, the Resolving Dependencies screen is displayed. Click Next to proceed.
On the Installation Status and Create Icons screen, do not make any changes. Click Finish to complete the installation process.
5.4 Configuring SSH
This section describes how to configure SSH and test your Cygwin setup after installing Cygwin on a host.
Note:
While configuring SSH, you may need to run thecygwin.bat script. While running cygwin.bat in Microsoft Windows Server 2008 and Microsoft Windows Vista, ensure that you invoke it in administrator mode. To do this, right-click the Sshd Service Linux
cygwin.bat file and select  Run as administrator.
Run as administrator.To configure SSH and test your Cygwin setup, follow these steps:
After you install Cygwin, navigate to the
C:cygwindirectory, open theCygwin.batfile in edit mode using any editor, and add the following line before invoking the bash shell.set CYGWIN=binmode ntsecFor example, here are the contents for the
Cygwin.batfile after adding the above line:To verify if Cygwin (
cygrunsrv)is installed properly, runC:cygwinCygwin.bat, and execute the following command:If Cygwin is installed properly, then all the Cygwin help options are displayed on the screen. However, if this command returns an error message, then you may have to reinstall Cygwin.
To configure the SSHD service, run
C:cygwinCygwin.bat, and execute the following command:After running the command, you are prompted the following questions:
At this point, if you want to use the same name, that is
cyg_server,enterno.You are then prompted the following questions:However, if you want to use a different name, enter
yes.You are then prompted the following questions:If the configuration is successful, you will see the following message:
Backup the
c:cygwinetcpasswdfile and then use any editor to open the file in edit mode. Remove only those entries of the user that you will use to connect to the host on which you want to install a Management Agent. Ask the user to make a backup of thec:cygwinetcpasswdfile before editing.If the user that you are employing to connect to the host on which you want to install the Management Agent is a local user, run
C:cygwinCygwin.batand execute the following:If the user you are employing to connect to the host on which you want to install the Management Agent running is a domain user, run
C:cygwinCygwin.batand execute the following:
(Only if the Cygwin software you have installed is of version 1.7.32 or higher) Open
C:cygwinetcsshd_configin a text editor and add the following line to the end of the file:KexAlgorithms diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1(For a domain user only) If the user you are employing to connect to the host on which you want to install the Management Agent is a domain user, do the following to start the SSH daemon:
Right-click on My Computer, and select Manage.
In the Computer Management dialog box that appears, go to Services and Applications, and select CYGWIN sshd.
Right-click CYGWIN sshd and select Properties.
In the Properties dialog box, go to the Log On tab.
Here, specify the domain/user name and password. Click Apply.
Run
C:cygwinCygwin.bat, and execute the following:Note:
If/var/log/sshd.logdoes not exist, you do not have to execute the following commands:
Perform one of the following steps to start the SSH daemon:
Run
C:cygwinCygwin.batand execute the following command:/usr/sbin/sshdOR
Run
C:cygwinCygwin.batand execute the following command:cygrunsrv -S sshdOR
Perform these steps:
Right-click on My Computer, and select Manage.
In the Computer Management dialog box that appears, go to Services and Applications, and select CYGWIN sshd.
Click CYGWIN sshd, then click the Start button.
Note:
If the SSH daemon does not start up, view thec:cygwinvarlogsshd.logfile for information on why the start up failed.You can now test your Cygwin setup. Sonic hedgehoganne 28 online, free games.
To do this, go to a different machine (that has the
sshclient running), and execute the following command:For example,
This command will prompt you to specify the password. When you specify the correct password, the command should return the accurate date.
Note:
If you experience a process fork failure, memory leak error, or a file access error after configuring SSH, view the following website for a workaround:If you are unable to find a workaround for your problem, report your problem to the Cygwin community using the following website:
5.5 After Installing Cygwin and Configuring SSH
After installing Cygwin (as described in Section 5.3) and configuring SSH (as described in Section 5.4), follow these steps:
If the OMS host runs on a Microsoft Windows platform, perform the following on the OMS host:
Right click My Computer, then select Properties. In the window that appears, select Advanced system settings, then select Environment Variables. In the System Variables section, create the
CYGWINvariable, and specify its value asnodosfilewarningNote:
You do not need to restart the host after performing this step.Navigate to the Cygwin install directory (that is,
C:cygwinif you chose to install Cygwin in the default location), open theCygwin.batfile in edit mode using any editor, then edit the following line:For example, these are the contents of the
Cygwin.batfile after editing the above line:From the Start menu, select Run. For Open, enter
services.msc,then click OK. Search for the Cygwin SSHD service and stop it.Navigate to the Cygwin install directory (that is,
C:cygwinif you chose to install Cygwin in the default location), then runCygwin.bat.Run the following command to start the SSHD service:Note:
Running this command may return an error mentioning that/var/emptymust be owned by the root user. If you encounter this error, run the following from the Cygwin terminal:After running this command, retry the
$ /usr/sbin/sshdcommand.
Perform the tasks mentioned in Step 1 on all the Microsoft Windows target hosts (on which you want to install Management Agents using the Add Host Targets Wizard or EM CLI).
Introduction
OpenSSH is a powerful collection of tools for the remote control of, and transfer of data between, networked computers. You will also learn about some of the configuration settings possible with the OpenSSH server application and how to change them on your Ubuntu system.
OpenSSH is a freely available version of the Secure Shell (SSH) protocol family of tools for remotely controlling, or transferring files between, computers. Traditional tools used to accomplish these functions, such as telnet or rcp, are insecure and transmit the user’s password in cleartext when used. OpenSSH provides a server daemon and client tools to facilitate secure, encrypted remote control and file transfer operations, effectively replacing the legacy tools.
The OpenSSH server component, sshd, listens continuously for client connections from any of the client tools. When a connection request occurs, sshd sets up the correct connection depending on the type of client tool connecting. For example, if the remote computer is connecting with the ssh client application, the OpenSSH server sets up a remote control session after authentication. If a remote user connects to an OpenSSH server with scp, the OpenSSH server daemon initiates a secure copy of files between the server and client after authentication. OpenSSH can use many authentication methods, including plain password, public key, and Kerberos tickets.
Installation
Installation of the OpenSSH client and server applications is simple. To install the OpenSSH client applications on your Ubuntu system, use this command at a terminal prompt:
To install the OpenSSH server application, and related support files, use this command at a terminal prompt:
Configuration

You may configure the default behavior of the OpenSSH server application, sshd, by editing the file /etc/ssh/sshd_config. For information about the configuration directives used in this file, you may view the appropriate manual page with the following command, issued at a terminal prompt:
There are many directives in the sshd configuration file controlling such things as communication settings, and authentication modes. The following are examples of configuration directives that can be changed by editing the /etc/ssh/sshd_config file.
Tip
Prior to editing the configuration file, you should make a copy of the original file and protect it from writing so you will have the original settings as a reference and to reuse as necessary.
Copy the /etc/ssh/sshd_config file and protect it from writing with the following commands, issued at a terminal prompt:
Furthermore since losing an ssh server might mean losing your way to reach a server, check the configuration after changing it and before restarting the server:
The following are examples of configuration directives you may change:
- To set your OpenSSH to listen on TCP port 2222 instead of the default TCP port 22, change the Port directive as such:
Port 2222
- To make your OpenSSH server display the contents of the
/etc/issue.netfile as a pre-login banner, simply add or modify this line in the/etc/ssh/sshd_configfile:
Banner /etc/issue.net
After making changes to the /etc/ssh/sshd_config file, save the file, and restart the sshd server application to effect the changes using the following command at a terminal prompt:
Warning
Many other configuration directives for sshd are available to change the server application’s behavior to fit your needs. Be advised, however, if your only method of access to a server is ssh, and you make a mistake in configuring sshd via the /etc/ssh/sshd_config file, you may find you are locked out of the server upon restarting it. Additionally, if an incorrect configuration directive is supplied, the sshd server may refuse to start, so be extra careful when editing this file on a remote server.
SSH Keys
SSH allow authentication between two hosts without the need of a password. SSH key authentication uses a private key and a public key.
To generate the keys, from a terminal prompt enter:
This will generate the keys using the RSA Algorithm. At the time of this writing, the generated keys will have 3072 bits. You can modify the number of bits by using the -b option. For example, to generate keys with 4096 bits, you can do:
During the process you will be prompted for a password. Simply hit Enter when prompted to create the key.
By default the public key is saved in the file ~/.ssh/id_rsa.pub, while ~/.ssh/id_rsa is the private key. Now copy the id_rsa.pub file to the remote host and append it to ~/.ssh/authorized_keys by entering:
Finally, double check the permissions on the authorized_keys file, only the authenticated user should have read and write permissions. If the permissions are not correct change them by:
You should now be able to SSH to the host without being prompted for a password.
Import keys from public keyservers
These days many users have already ssh keys registered with services like launchpad or github. Those can be easily imported with:
The prefix lp: is implied and means fetching from launchpad, the alternative gh: will make the tool fetch from github instead.
Two factor authentication with U2F/FIDO
OpenSSH 8.2 added support for U2F/FIDO hardware authentication devices. These devices are used to provide an extra layer of security on top of the existing key-based authentication, as the hardware token needs to be present to finish the authentication.
It’s very simple to use and setup. The only extra step is generate a new keypair that can be used with the hardware device. For that, there are two key types that can be used: ecdsa-sk and ed25519-sk. The former has broader hardware support, while the latter might need a more recent device.
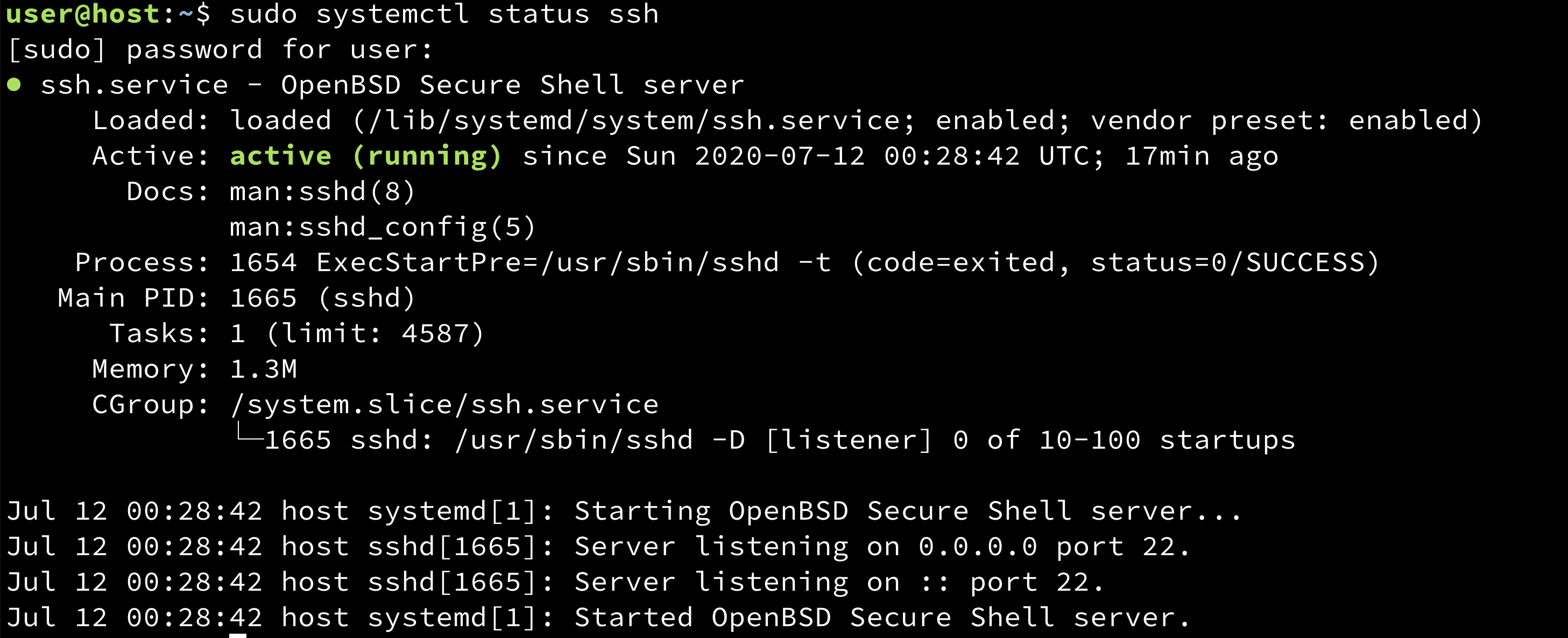
Sshd Service Logs
Once the keypair is generated, it can be used as you would normally use any other type of key in openssh. The only requirement is that in order to use the private key, the U2F device has to be present on the host.
Sshd Service Status
For example, plug the U2F device in and generate a keypair to use with it:
Contact | bioengaging technology: dr. kevin culpepper. Now just transfer the public part to the server to ~/.ssh/authorized_keys and you are ready to go:
References
Ubuntu Wiki SSH page.
Last updated 8 months ago. Help improve this document in the forum.
